Current Projects
- IoT Attacks and Defenses (DSN'20, USENIX Security'21, NDSS'21, RAID'21, ACSAC'21, Oakland'22, DSN'22, USENIX Security'23, MobiSys'23)
- IoT Pairing and Authentication (MobiCom'19, CCS'20, MobiSys'22, MobiCom'22, UbiComp'22, TDSC'22, TMC'24)
- Natural Language Processing Inspired Binary Code Analysis (NDSS'19, USENIX Security'23)
- Adversarial Machine Learning (DSN'19, RAID'19, ACSAC'20, AsiaCCS'21)
Past Projects
- Insecurity Analysis of Middleware on Mobile Platforms (MobiSys'17, TMC'19)
- Android Application Repackaging and Tampering Detection (CGO'18, TDSC'19)
- Wolverine: A Self-evolving Business Continuity Protector (DSN'15, DSN'19)
- DeltaPath: Precise and Scalable Calling Context Encoding (CGO'14)
- Kruiser: A Concurrent Kernel Heap Protector (NDSS'12)
- Cruiser: A Lock-free Concurrent User-space Memory Monitor (PLDI'11)
- Safe Query Processing in Multi-party Distributed Databases (TKDE)
Software Release
- Fuzzing assisted dynamic symbolic execution: the first IoT-app fuzzer in the literature (ACSAC'21)
- Erase-and-Restore: Accurate and Model-Agnostic Detection of L2 Adversarial Examples (AsiaCCS'21)
- InnerEye: Neural Machine Translation Inspired Binary Code Similarity Comparison (NDSS'19)
- MVP-Ears: Multiversion Programming Inspired Detection of Audio Adversarial Examples (DSN'19)
- AEPecker: Detecting and Rectifying L0 Adversarial Examples (RAID'19)
- Centaur: Symbolic Execution of Android Framework for Vulnerability Discovery and Exploit Generation (MobiSys'17)
- Cruiser: A Shared Library Protecting Your Heap Memory Transparently and Efficiently (PLDI'11)
Note: the list below is out of date and does NOT reflect my current research interests; please check out my publications to learn my recent researches.
Wolverine: A Self-evolving Business Continuity Protector
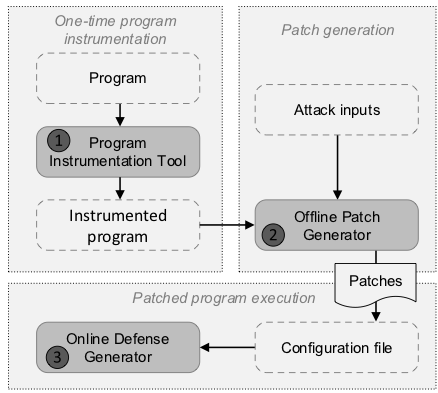
Bill Gates said "Microsoft products are generally bug free", while in parctice it is very unlikely to build bug-free software. Software bugs lead to repeated software execution crashes and data loss, which keep hurting business continuity and reputation. Business owners can do little but suffer monetary loss until the software gets patched. Attackers can even blackmail the business owners with the threat of denial-of-service attacks exploiting the crashes. Today's software execution lacks an effective mechanism that can prevent or mitigate such repetitive failure and crashes.
Our goal is to deliver a technology that learns from the historical failures and evolves itself to prevent any further repetitive crashes. The technology aims to protect software execution and significantly improve business continuity. It should largely promote the image of software producers and the confidence of business owners in their systems.
Stories...
I proposed the idea and have been leading the project. Mingyi Zhao, Dr. Peng Liu and I are working on it intensively.
Related Publications:
| DSN 2019 |
"HeapTherapy+: Efficient Handling of (Almost) All Heap Vulnerabilities Using Targeted Calling-Context Encoding." Qiang Zeng, Golam Kayas, Emil Mohammed, Lannan Luo, Xiaojiang Du, and Junghwan Rhee. The 49th IEEE/IFIP International Conference on Dependable Systems and Networks, 2019. >> [PDF] [Slides] |
| DSN 2015 |
"HeapTherapy: An Efficient End-to-end Solution against Heap Buffer Overflows" Qiang Zeng*, Mingyi Zhao*, and Peng Liu. ( *co-first author ) 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, 2015. >> [PDF] |
| Oakland 2014 |
"Targeted Therapy for Software Failures and Vulnerabilities." (Poster) Qiang Zeng, Mingyi Zhao, and Peng Liu. 35th IEEE Symposium on Security and Privacy (Poster Session), 2014. |
DeltaPath: Precise and Scalable Calling Context Encoding
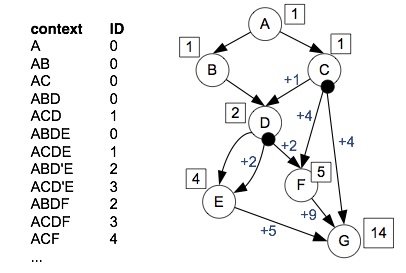
A calling context is the sequence of active function/method invocations that lead to a program location. It provides critical information about dynamic program behavior. The usage has been demonstrated in a wide range of applications, such as debugging, event logging and error reporting, testing, attack and anomaly detection, performance optimization, and profiling.
A few techniques have been proposed to track calling context efficiently. However, they either lack a reliable and precise decoding capability; or only work under restricted conditions, that is, small programs without object-oriented programming or dynamic component loading. We propose an encoding technique without those limitations. It provides precise and reliable decoding, supports large-sized programs, both procedural and object-oriented ones, and can cope with dynamic class/library loading.
We have implemented DeltaPath as a Java agent, which can work with any JVM compatible with JDK 5.0. The evaluation on SPECjvm shows that its efficiency is comparable with that of the state-of-the-art approach while our technique provides precise decoding demonstrating scalability and flexibility.
Stories...
The project was mainly done when I worked as a research intern in NEC Laboratories America, mentored by Dr. Junghwan Rhee. Initially Dr. Rhee and I just wanted to do encoding relative to a set of logging points, and thought it should be straightforward. Soon I found the problem was much more challenging, as the encoding technique we applied could not deal with virtual functions or dynamic class loading, while other existing encoding techniques lacked a reliable decoding capability. The engineering-style work became a serious research project. The task was tough though, not only because I had zero Java coding experience before, but also due to the nature of the challenges we tried to solve. The algorithm design and system implementation were mainly finished by me and I also helped evaluate it.
Related Publications:
| CGO 2014 |
"DeltaPath: Precise and Scalable Calling Context Encoding." Qiang Zeng, Junghwan Rhee, Hui Zhang, Nipun Arora, Guofei Jiang, and Peng Liu. Symposium on Code Generation and Optimization (CGO), 2014. |
| Patent 2013 |
"Method for Guarding a Monitoring Scope and Interpreting Partial Control Flow Contex." Junghwan Rhee, Hui Zhang, Nipun Arora, Geoff Jiang, and Qiang Zeng. Provisional application No.: 61/805,809, filed 2013. |
| Patent 2012 |
"Log-driven Deployed Systems Monitoring with Relative Calling Context Encoding." Junghwan Rhee, Hui Zhang, Nipun Arora, Geoff Jiang, Kenji Yoshihira, and Qiang Zeng. Provisional application No.: 61/694,009, filed 2012. |
Kruiser: A Concurrent Kernel Heap Protector
Kernel heap buffer overflow vulnerabilities have been exposed for decades, but there are few practical countermeasure that can be applied to OS kernels. Previous solutions either suffer from high performance overhead or compatibility problems with mainstream kernels and hardware.
We present Kruiser, a concurrent kernel heap buffer overflow monitor in cloud computing platforms. Kruiser migrates security enforcement from the kernel’s normal execution to a concurrent monitor process, leveraging the increasingly popular multi-core architectures. To reduce the synchronization overhead between the monitor process and the running kernel, we design a novel semi-synchronized nonblocking monitoring algorithm, which enables efficient runtime detection on live memory without incurring false positives.
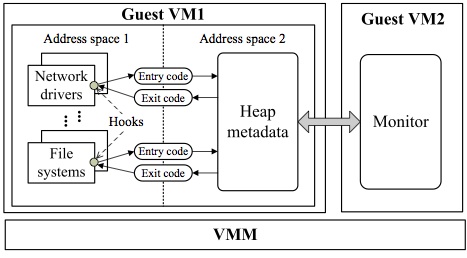
To prevent the monitor process from being tampered and provide guaranteed performance isolation, we utilize the virtualization technology to run the monitor process out of the monitored VM, while heap memory allocation information is collected inside the monitored VM in a secure and efficient way. The hybrid VM monitoring technique combined with the secure canary that cannot be counterfeited by attackers provides guaranteed overflow detection with high efficiency.
We have implemented a prototype of Kruiser based on Linux and the Xen hypervisor. The evaluation shows that Kruiser can detect realistic kernel heap buffer overflow attacks effectively with minimal overhead.
Stories...
Protecting kernel heap in a concurrent fashion was described as the future work of the Cruiser paper. Kernel heap buffer allocation differs from the application peer, so it requires new ideas and solutions for protection. I proposed the version-based heap page checking algorithm to achieve an efficient non-blocking heap corruption checking. To avoid the attacker to manipulate the canary, I proposed the concept of Secure Canary leveraging cryptography. An early version of the paper was rejected due to the lack of protection for the metadata collected by Kruiser. Inspired by the Secure-In-VM Monitoring technology, I proposed a novel hybrid technique combining out-of-VM monitoring and in-VM interposition to protect the integrity of the metadata. In short, the road to finish the project was paved with challenges and fun to conquer them. The implementation and evaluation were mainly contributed by Donghai Tian.
Related Publications:
| NDSS 2012 |
"Kruiser: Semi-synchronized Non-blocking Concurrent Kernel Heap Buffer Overflow Monitoring." Donghai Tian, Qiang Zeng, Dinghao Wu, Peng Liu, and Changzhen Hu. 19th Annual Network and Distributed System Security Symposium (NDSS), 2012. >> [PDF] [Slides] |
Cruiser: A Lock-free Concurrent Application Memory Monitor
Security enforcement inlined into user threads often delays the protected programs; inlined resource reclamation may interrupt program execution and defer resource release. We propose software cruising, a novel technique that migrates security enforcement and resource reclamation from user threads to a concurrent monitor thread. The technique leverages the increasingly popular multicore and multiprocessor architectures and uses lock-free data structures to achieve non-blocking and efficient synchronization between the monitor and user threads.
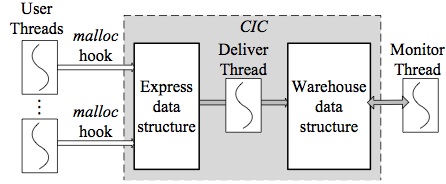
As a case study, software cruising is applied to the heap buffer overflow problem. Previous mitigation and detection techniques for this problem suffer from high performance overhead, legacy code compatibility, semantics loyalty, or tedious manual program transformation. We present a concurrent heap buffer overflow detector, CRUISER, in which a concurrent thread is added to the user program to monitor heap integrity, and custom lock-free data structures and algorithms are designed to achieve high efficiency and scalability.
The experiments show that our approach is practical: it imposes an average of 5% performance overhead on SPEC CPU2006, and the throughput slowdown on Apache is negligible on average.
Stories...
The idea of utilizing idle processor cores to scan heap was proposed by Dr. Dinghao Wu. To make the concurrent memory monitoring idea fly, Dr. Dinghao Wu, Dr. Peng Liu and I tried a series of data structures, for example, a lock-based red-black tree and a lock-free hash table, but the efficiency was not satisfactory. We were completely stuck after numerous failures, but didn't give up. One day I realized that a most simple one-producer one-consumer wait-free ring buffer might have magic power. After that we made quick progress. The self-adaptive ring chain resolved the loss of buffer addresses. By setting up a tombstone flag for each buffer free and strategically recovering from segfault, the slowdown due to buffer deallocation was avoided. With less then one month, I resolved those challenges, designed the custom lock-free data structures and non-blocking algorithm, and built the system. The PLDI reviewers uniformly praised highly on the engineering quality of the work.
Related Publications:
| PLDI 2011 |
"Cruiser: Concurrent Heap Buffer Overflow Monitoring Using Lock-free Data Structures." Qiang Zeng, Dinghao Wu, and Peng Liu. 32nd ACM SIGPLAN Conference on Programming Language Design and Implementation (PLDI), 2011. >> [PDF] [Slides] |
| Book Chapter 2013 |
"Software Cruising: A New Technology for Building Concurrent Software Monitor." Dinghao Wu, Peng Liu, Qiang Zeng, and Donghai Tian. Secure Cloud Computing, Advances in Information Security Series, Springer, 2013. |
Safe Query Processing in Multi-party Distributed Databases
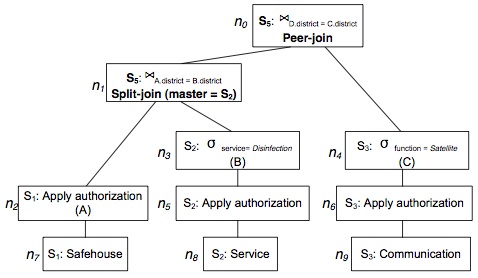
In a federated database system, each independent party exports some of its data to the system for information sharing. The information sharing in such system is very inflexible, as all peer parties access the same set of data exported by a party, while the party may want to authorize different portions of its information accessible to different peer parties. Such authorization autonomy may be achieved by pulling the raw data to the querier and performing centralized query computation, which, however, usually leads to high communication costs.
We propose a novel query evaluation scheme that supports the authorization autonomy with decentralized query processing. Our query planning algorithm adopts a new join method, named split-join, along with other safe join methods; it reduces the communication cost by pushing partial query computation to data sources without violating the access control. The proofs of the correctness and safety of the algorithm are presented. The evaluation demonstrates that the scheme significantly saves the communication cost in a variety of circumstances and settings.
Stories...
The main part of the work was done when I worked a research intern in IBM T. J. Watson Research Center. My mentor was Dr. Jorge Lobo, who proposed a new join method that may save the communication cost significantly. We then worked closely and explored safe and efficient query processing in a multi-party database system. In this project I did the problem formalization, designed the query processing algorithm, and proved its correctness.
Related Publications:
| TKDE |
"Enforcement of Autonomous Authorizations in Collaborative Distributed Query Evaluation." Qiang Zeng, Mingyi Zhao, Peng Liu, Poonam Yadav, Seraphin Calo, and Jorge Lobo. IEEE Transactions on Knowledge and Data Engineering (TKDE), 2014. >> [PDF] |
| ACITA 2012 |
"Safe Query Processing for Pairwise Authorizations in Coalition Networks." Qiang Zeng, Jorge Lobo, Peng Liu, Seraphin Calo, and Poonam Yadav. 6th Annual Conference of International Technology Alliance (ACITA), 2012. >> [PDF] [Slides] |